![]()
Medical tech startups are regulated by the FDA and must abide by strict regulations at all times. For example, all medical devices must be approved by the FDA. Acting outside of the FDA’s regulations can result in harsh penalties including fines and even jail time.
Whether your medical tech startup produces low-risk or high-risk devices, compliance is a crucial and complex necessity.
1. Stay on top of regulatory changes
If you don’t stay on top of regulatory changes you could be in trouble. For example, the recently adopted GDPR regulations threw a wrench in every business owner’s compliance protocols. Businesses owners had a short period of time to comply before penalties would be legally assessed for violations.
The same can happen in the medical tech world. One day, you might be comfortable with the current regulations and the next day there’s a new regulation you need to comply with. Or, a current regulation might be amended.
The best way to stay ahead is to stay on top of proposed changes in regulatory compliance. Nothing becomes law overnight without a process beforehand.
2. Warn patients not to mix-and-match components
It’s important to warn against swapping out unauthorized device components for any reason. Patients may not understand why they shouldn’t use other components with their device. It’s critical to warn that using unauthorized components can result in injury and/or death, depending on your device. These warnings should be placed in the box for patients and in the literature given to health care providers.
Patients need to understand that the FDA authorizes medical devices for a specific use even when there are multiple components involved. For example, an automatic insulin dosing system comes with several authorized components including an insulin pump, a glucose monitoring system, and an algorithm that determines the dose of insulin. These three devices are tested and authorized together as a complete system.
Sometimes patients decide to mix-and-match components from other systems (or they buy a cheaper, unauthorized component to replace one that broke) and it doesn’t work correctly and ends up harming the patient. For example, the FDA received a report of a serious adverse event related to a blood glucose monitoring system. The system was used with an unauthorized component and resulted in an insulin overdose.
3. Keep a tight watch on your electronic record practices
According to Title 21 (Part 11) of the Code of Federal Regulations, all computer systems used to create, modify, and maintain electronic records and signatures (including mobile devices) are subject to FDA validation. All hardware and software must be readily available at all times for FDA inspection. Arbour Group explains 13 key elements of these regulations including:
- Validation of systems to ensure accuracy, reliability, consistent intended performance and the ability to discern invalid or altered records.
- Ability to generate accurate and complete copies of records in both human readable and electronic form suitable for inspection, review and copying.
- Protection of records to enable accurate and ready retrieval throughout the record retention period.
- Limiting access to authorized individuals.
- The use of secure, computer-generated, time-stamped audit trails to independently record the date and time of operator entries.
- Record changes shall not obscure previously recorded information and audit trails are to be maintained as long as the associated electronic record.
- And more
Handling electronic records according to regulations can’t be done on a whim. Compliance requires a strict system that uses software to restrict access and secure records, among other tasks. Compliance with electronic records regulations are complex. The stakes are too high; there’s no room for mistakes.
4. Be absolutely certain if you don’t think your product qualifies as a device
When you think of medical devices, you probably think of pacemakers, syringes, and nebulizers. However, even a simple tongue depressor is considered a medical device and subject to FDA regulations.
Whether or not something is considered a medical device is determined by The Federal Food Drug & Cosmetic Act. In summary, a product is considered a medical device when:
- The device is used in the process of diagnosing, treating, or preventing a disease or condition. Tongue depressors meet this qualification.
- The device is intended to affect the structure or function of the body without chemical action. This qualification separates drugs from medical devices.
If you’re not sure if your product is a medical device, head over to the FDA’s CDRH Classification Database to review products the FDA considers devices. If you find something that matches your product, it’s probably considered a medical device and is regulated by the FDA.
5. Don’t go to market without a pre-market application
There are two ways you can bring your product to market, but just launching on your own isn’t one of them. If your medical device is considered a Class III device, you’ll need to go through the Pre-Market Approval (PMA) process. If your device is a Class I or II device, you’ll go through the 510(k) process.
With the 501(k) process, you must demonstrate the device is “substantially equivalent” to a previous device. If this is the path you must take, you’ll need bench testing data and a small clinical study. The process may only take a few months.
The PMA process is more involved. You’ll need to perform larger, multi-center, randomized clinical trials to obtain your data. You can expect to involve hundreds or thousands of patients in your trials and it will likely cost in the tens of millions of dollars.
The FDA is strict with PMAs and in 2012, only approved 37.
6. Know that apps aren’t automatically exempt from regulations
Health apps are abundant, claiming to measure your pulse, heartrate, and some apps even claim to help you lose weight. It’s unclear whether these apps are accurate or just for fun, but the FDA doesn’t care – when an app claims to do something that is also accomplished by a medical device, the app might require regulation.
The FDA announced they don’t plan to review all medical apps but will stay focused on apps designed for use with FDA-approved medical devices. However, that doesn’t mean you’re off the hook.
Apps are hot, but before launching a health-related app, find out if it requires regulation. It might sound silly now, but if a consumer misuses your app in the future and suffers harm, they might end up suing you.
7. Stay caught up with medical device lawsuits
Stay caught up with medical device lawsuits as a reminder that details do matter, and violations are enforced.
When you send out your weekly or monthly newsletter to your team, include a section for recent news. Use that section to make your team aware of any current lawsuits, fines, and other penalties paid by companies who chose to ignore compliance regulations. Keep the reality in their awareness so they’re not tempted to take shortcuts or forge data behind your back.
Medical device lawsuits are abundant. For example, in December 2018, Minnesota-based medical device manufacturer ev3 agreed to plead guilty and pay $17.9 million for disregarding safety laws. The company distributed a neurovascular medical device called Onyx. Onyx, a liquid embolization device, was originally approved by the FDA for use inside the brain.
According to the FDA, between 2005-2009, sales reps from ev3 encouraged surgeons to use Onyx outside the brain in unproven and dangerous ways. The company was told they need to perform a study to get those uses approved, but the company ignored the warnings. The company incentivized sales reps to promote unauthorized uses and the sales reps even attended surgical procedures where they instructed surgeons on what to do.
8. Prepare to conform to regulation changes
It’s possible that your device’s technology might be ahead of current regulations. If you’re an innovator, expect to be required to comply with regulations you may not have needed to comply with when you first launched.
Be aware that regulatory changes in the European Union and Canada can affect your company in the United States. For example, the Medical Device Single Audit Program (MDSAP) was adopted in the U.S., Brazil, Canada, Japan, and Australia. This program is designed to enhance product quality and safety and help determine the lifecycle of a product.
The MDSAP program also changes the way inspections are performed, so be ready and willing to do things differently when required.
Don’t move forward before you’re ready
Avoid troubling situations by following regulation requirements from the start. Don’t procrastinate or skip any duties you have to the public. Don’t announce your device’s efficacy before the data comes in. Know for sure before you start marketing your device. It’s tempting to start marketing before your trials have been completed, but if the data doesn’t live up to your expectations you’ll be in a bad situation. You’ll either need to lie to move forward, or admit a mistake to make things right.
If you need more time to conduct trials and studies, take that time. People feel better about using medical devices when there’s strong evidence they’re safe and effective.
https://samplecic.ch/regulatory-tips-for-medical-tech-startups-regulated-by-the-fda.html









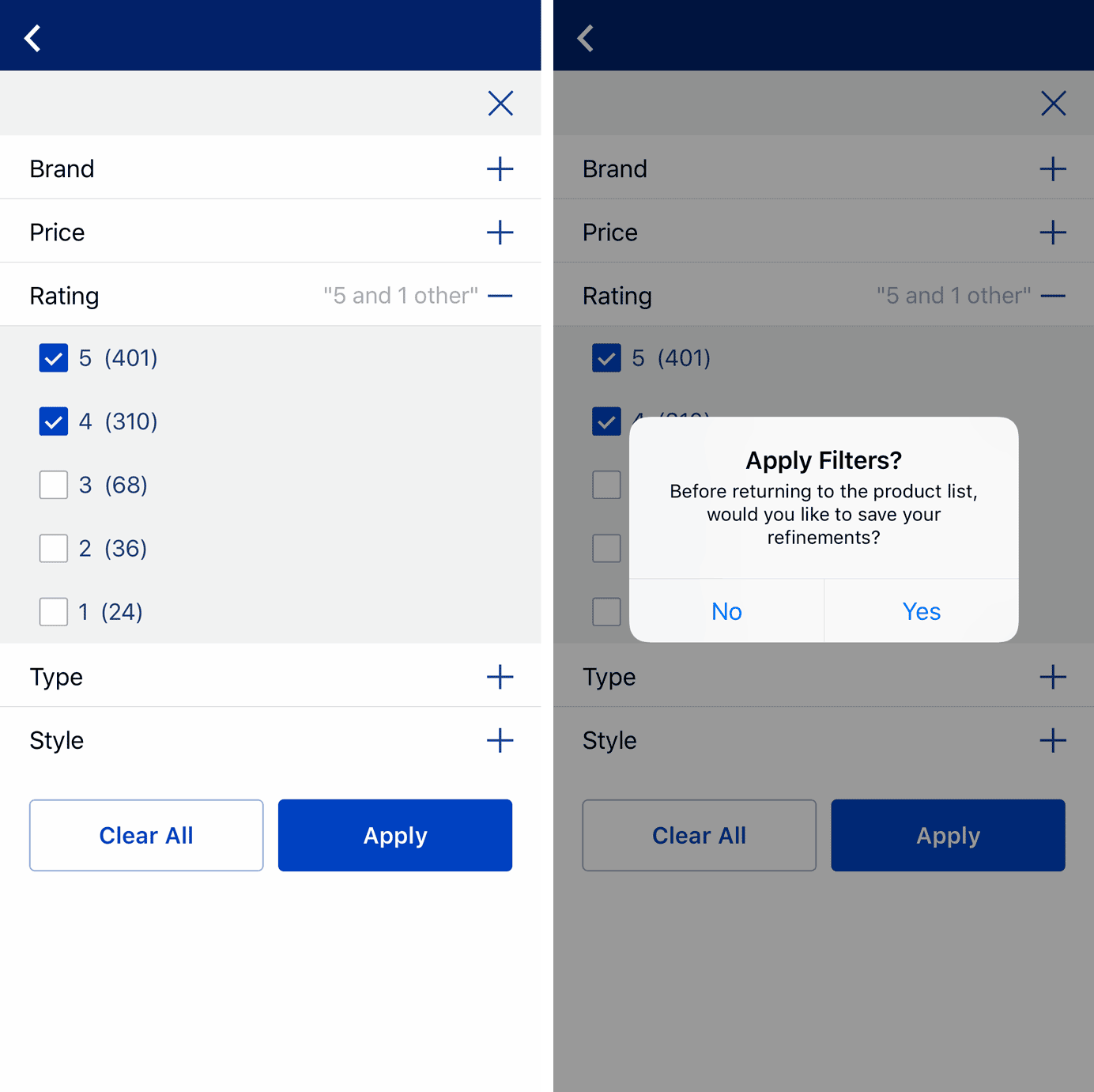 Lowes mobile app: Tapping either the X button or the Back arrow could reset any selections and take the user back to the previous result set. Right: After tapping X, a confirmation dialog appeared to check whether the user meant to apply or cancel the filter refinements before returning to the results list.
Lowes mobile app: Tapping either the X button or the Back arrow could reset any selections and take the user back to the previous result set. Right: After tapping X, a confirmation dialog appeared to check whether the user meant to apply or cancel the filter refinements before returning to the results list.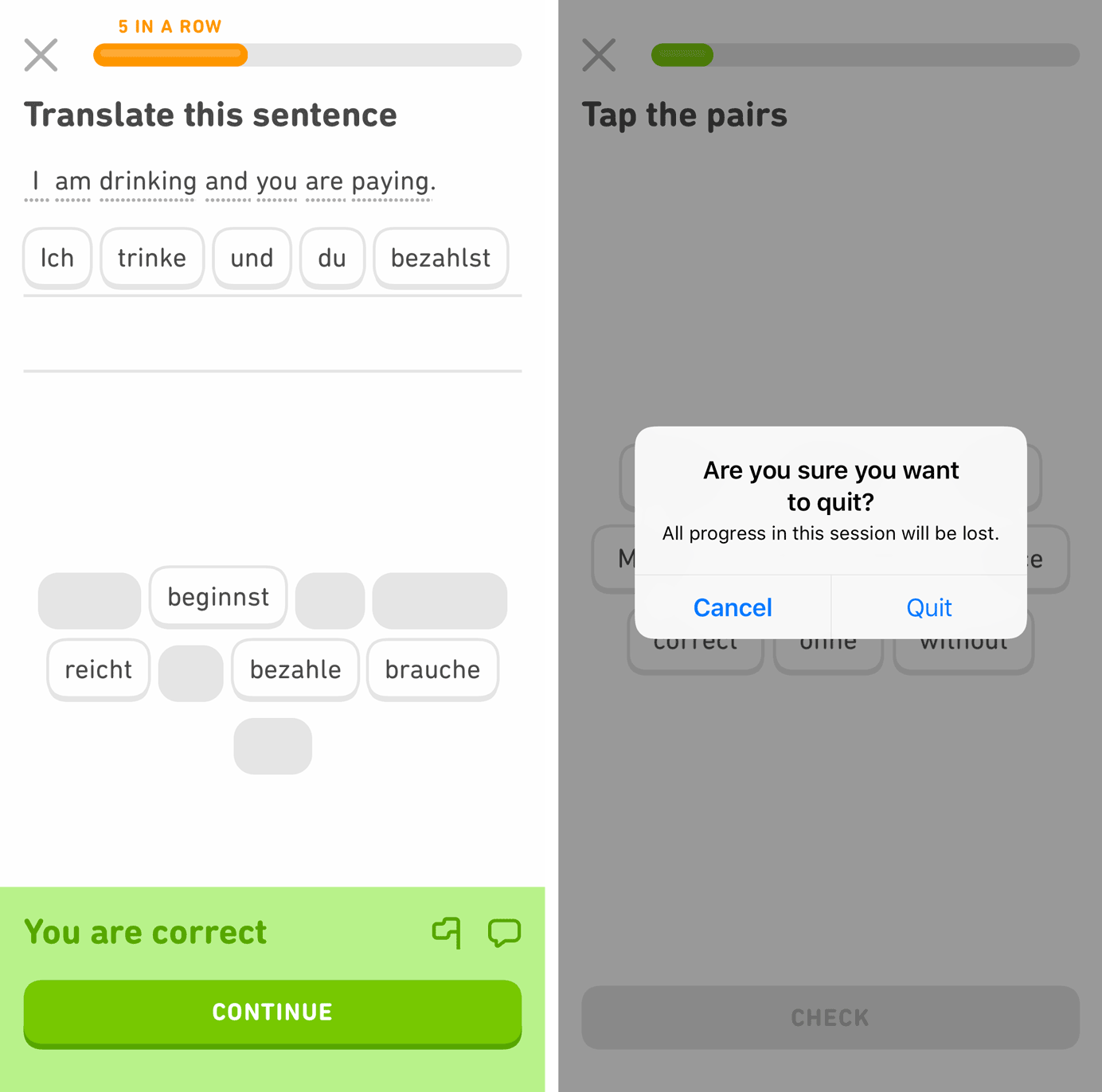 Duolingo: Clicking the X button would end the current lesson and forfeit any progress. To guard against mistakes, the app included a confirmation dialog.
Duolingo: Clicking the X button would end the current lesson and forfeit any progress. To guard against mistakes, the app included a confirmation dialog.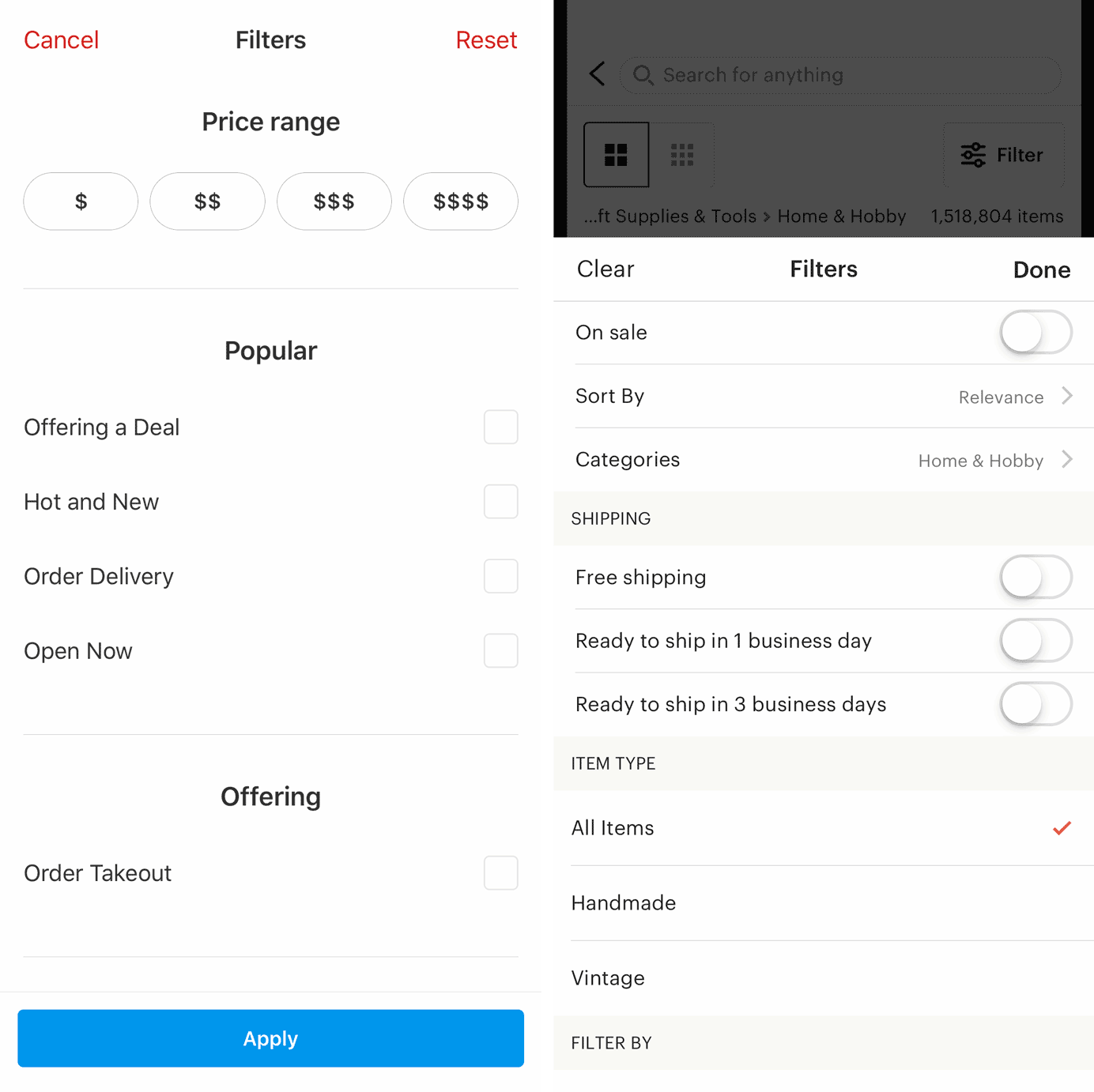 (Left) Yelp mobile app: Text labels for Cancel, Reset, and Apply were direct and clear, making it less likely that users would inadvertently close the view and lose their filter selections. (Right) Etsy mobile app: The text label Clear gave a clear way (pardon the pun) for users to cancel their selections. The Done link returned to the product-listings page, with the selections already applied. 3. Favor Close & Save
(Left) Yelp mobile app: Text labels for Cancel, Reset, and Apply were direct and clear, making it less likely that users would inadvertently close the view and lose their filter selections. (Right) Etsy mobile app: The text label Clear gave a clear way (pardon the pun) for users to cancel their selections. The Done link returned to the product-listings page, with the selections already applied. 3. Favor Close & Save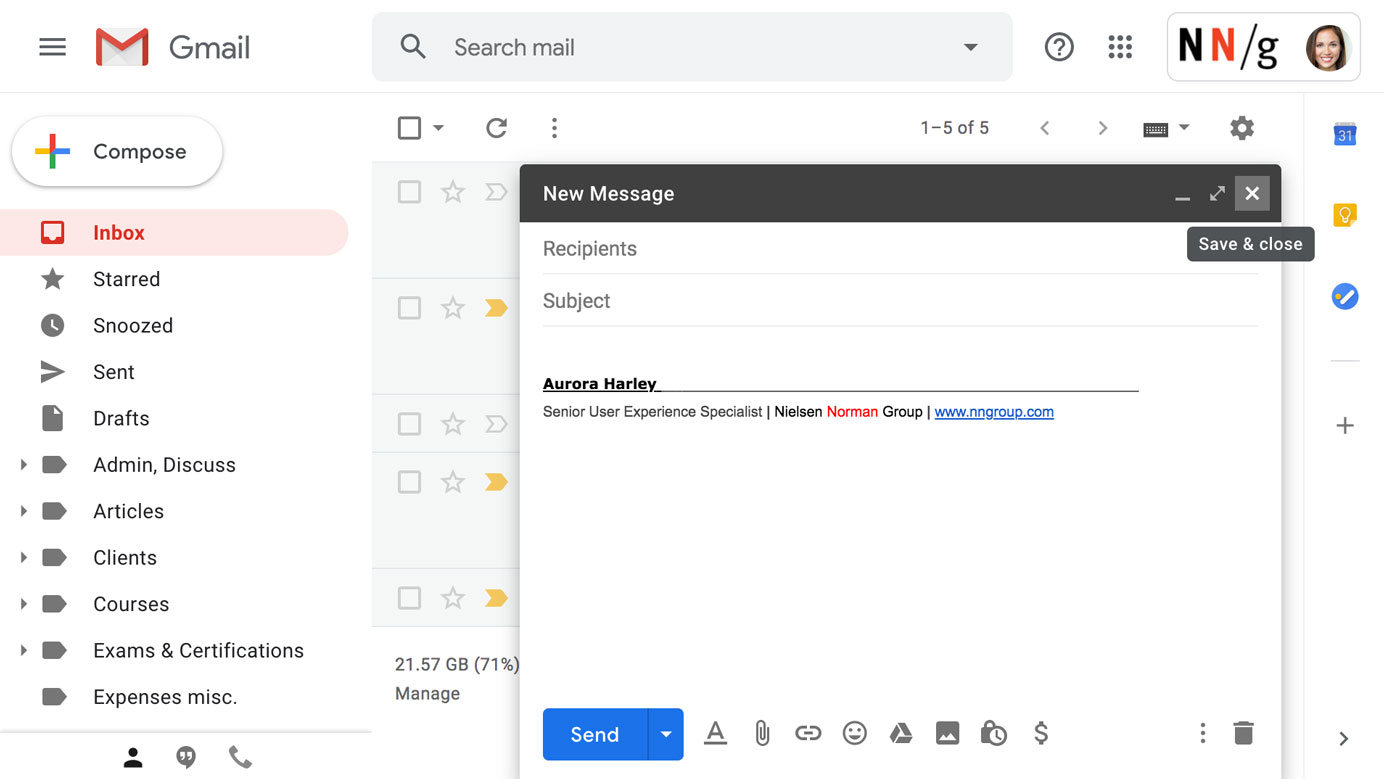 Gmail: Hover revealed that the X icon was for dismissing the window and not for deleting the draft, allowing users to Save & close the message window without losing work in progress.
Gmail: Hover revealed that the X icon was for dismissing the window and not for deleting the draft, allowing users to Save & close the message window without losing work in progress.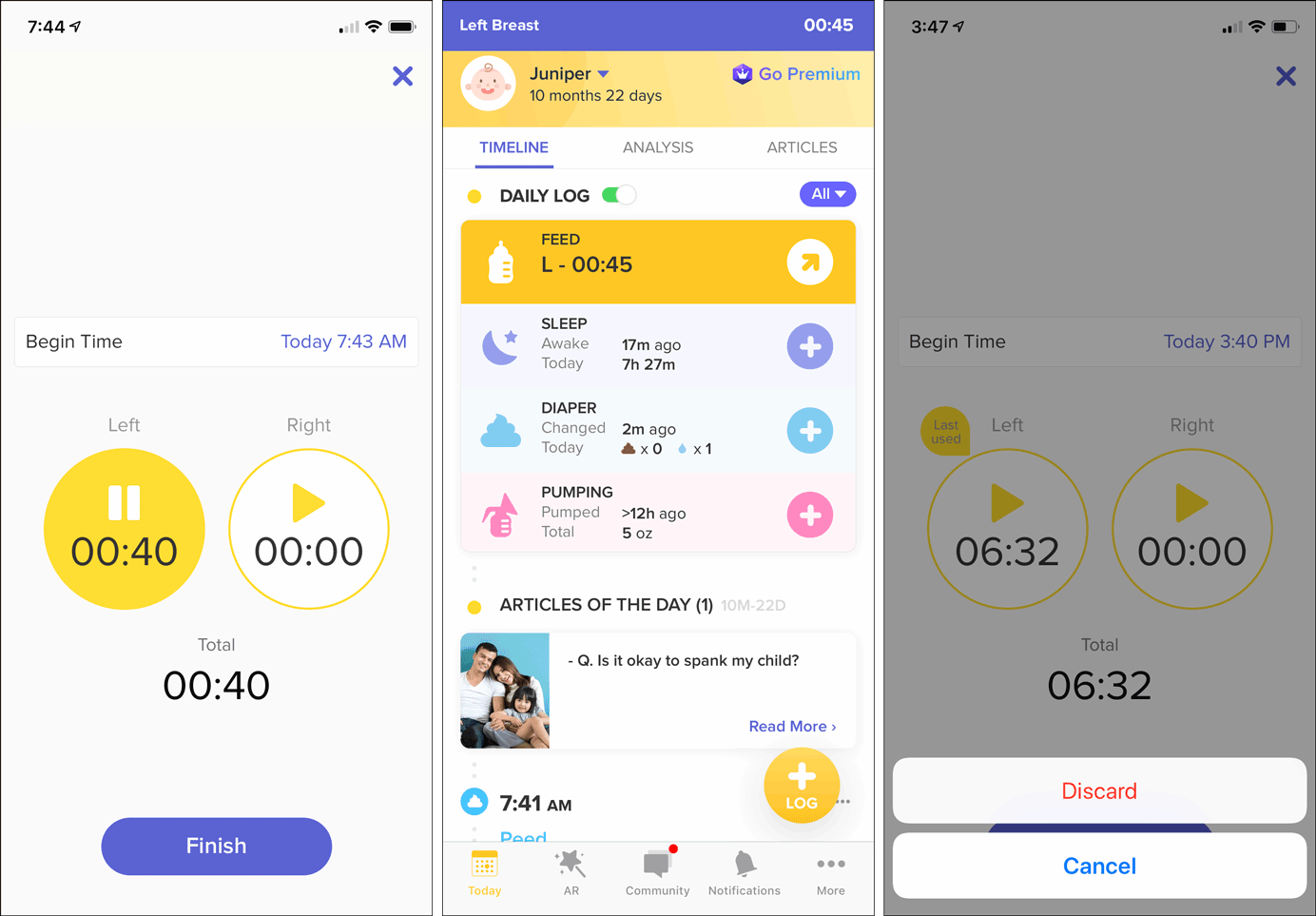 Glow Baby: (Left) Tapping the X icon in a running-timer view dismissed the view without canceling the timer, and thus, allowed the user to continue using the app to log other types of events, participate in the community discussions, read articles, and so on. (Middle) The status for the running timer was displayed in a banner at the top of the screen. (Right) Hitting the X while the timer was paused brought up the Discard or Cancel buttons to detect the user’s intention.
Glow Baby: (Left) Tapping the X icon in a running-timer view dismissed the view without canceling the timer, and thus, allowed the user to continue using the app to log other types of events, participate in the community discussions, read articles, and so on. (Middle) The status for the running timer was displayed in a banner at the top of the screen. (Right) Hitting the X while the timer was paused brought up the Discard or Cancel buttons to detect the user’s intention.